blog

The poem of Kaiji
by Vlad O & Daniel C
In recent years, there has been a concerning trend where cybersecurity experts themselves have increasingly become the targets of highly sophisticated attacks. These attacks often revolve around fake exploits associated with newly discovered vulnerabilities. Cybercriminals and state-sponsored actors have learned to exploit the urgency and interest that surrounds newly reported vulnerabilities, using this to their advantage in a dangerous game of deception.
These adversaries craft and distribute malicious files, often disguised as legitimate proof-of-concept (PoC) code. When unsuspecting cybersecurity professionals, intent on analyzing or mitigating these new threats, download and execute this code, they unknowingly compromise their own systems. This scenario highlights a disturbing irony: those tasked with defending against cyber threats are being manipulated into opening the very doors they are supposed to secure.
A Growing Concern
While these attacks are not a daily occurrence, there is a noticeable increase in attempts to breach the defenses of individuals responsible for evaluating vulnerabilities, adversarial tools, and PoC exploit code. The security community, which relies heavily on the shared analysis and mitigation of threats, is now facing an additional layer of risk. The attackers’ methods are becoming more refined, and their targets are those who play a critical role in the broader cybersecurity ecosystem.
The sophistication of these backdoors is particularly alarming. These are not mere malicious scripts or basic exploits that open a reverse shell. The intricate design and development of such backdoors suggest that attackers see a significant return on investment (ROI) in these efforts. This ROI is likely predicated on the assumption that many professionals, perhaps in their haste to respond to a new vulnerability, may run these malicious files without performing the necessary due diligence. The Technical Craftsmanship:
A Case in Point
A recent example of this trend involved the use of Golang as a tool for backdooring. Golang’s appeal lies in its ability to create statically linked binaries, which, while larger in size, offer a unique advantage in that they can operate independently of the target system’s environment. This makes detection and analysis more challenging, increasing the likelihood of successful exploitation.
However, for those who think ahead, there are even more covert methods available. For instance, utilizing a kernel module for persistence would be a more elegant approach. Kernel modules operate at a low level within the system, and as such, they often go unnoticed. How many truly check for such deep-seated intrusions? The reality is, very few.
Intro
In our previous post we explored the kill-chain and infection footprint of a piece of malware that was distributed through a “spiked” pseudo-exploit targeting the regreSSHion bug. This vulnerability, an unauthenticated remote code execution (RCE) flaw in OpenSSH’s server (sshd) on glibc-based Linux systems, presents a significant threat vector. Now, let’s shift our focus to a static analysis of the actual malware that gets deployed to the system post-infection.
The Infection Process: A Quick Recap
To briefly recap, the regreSSHion vulnerability allowed attackers to gain remote code execution capabilities without authentication, making it an ideal target for cybercriminals seeking to exploit Linux-based environments. The exploit was cleverly disguised to appeal to security researchers and system administrators, making them more likely to download and run it, thereby triggering the infection process.
Once the exploit successfully compromises a system, it deploys a malicious payload—this is where our analysis picks up.
The sample:
Filename: amd64
size: 5365912 bytes (5.1 MB)
md5: 2be087e54204a6c395e05516c53fd579
sha1: 3bdad143cd168a2015aba2053e53f99a24d52ace
sha256: b60ad90687871ae94e2b33cf2320f523ee614893215335dc5958a6a705488330
TLSH: T12a464a47fc9555a9d0aad231ca629263bb717c495b3023d32f90f7782f72bd0aa79340
Lest start by looking at the domain that this samples tries to resolve and communicate to after its execution, to set the context:
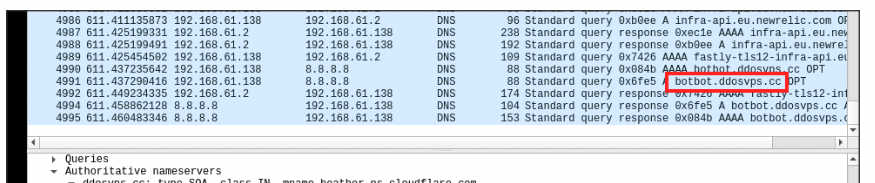
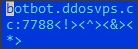
Domain enumeration - botbot.ddosvps.cc
The domain in question, along with its associated IP address, has been identified as a significant player in the command and control (C&C) operations of a sophisticated botnet. Notably, this IP has a history of involvement in various high-profile malware campaigns, including those associated with AgentTesla and the infamous Mirai Botnet. This history strongly suggests the involvement of a well-established threat actor, one with a deep expertise in orchestrating large-scale cyber attacks.
A Closer Look at the IP’s Malicious History
The association of this IP address with both AgentTesla and the Mirai Botnet is particularly concerning. AgentTesla is a notorious keylogger and information stealer that has been widely used in cyber espionage campaigns. Its role in stealing sensitive data from infected systems has made it a preferred tool for cybercriminals worldwide.
On the other hand, the Mirai Botnet, known for its unprecedented distributed denial-of-service (DDoS) attacks, has caused widespread disruption across the internet. Mirai’s modus operandi involves hijacking vulnerable IoT devices and using them to flood targeted systems with traffic, effectively overwhelming and incapacitating them. The connection of this IP address to Mirai hints at the potential for DDoS attacks, especially considering the scale and impact of Mirai’s previous operations.
botbot.ddosvps.cc
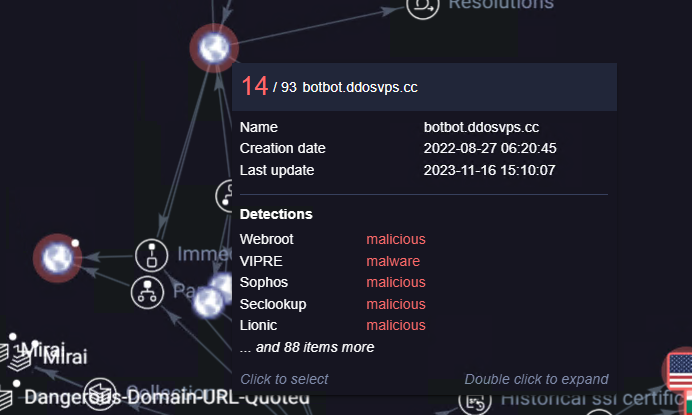
ddosvps.cc
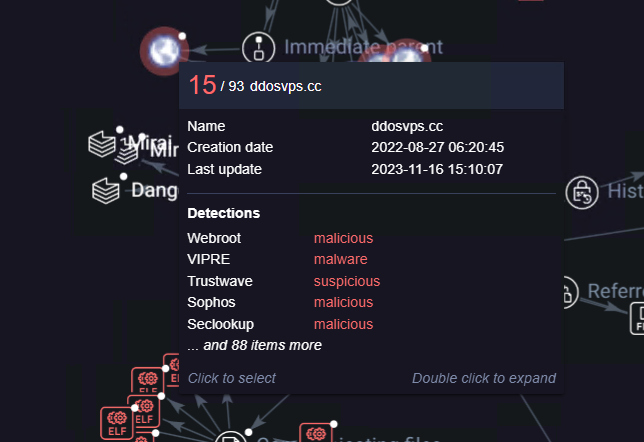
bot.ddosvps.cc
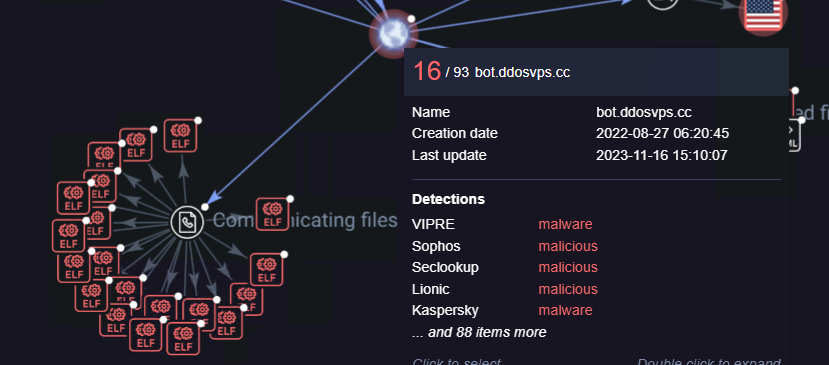
mirai samples
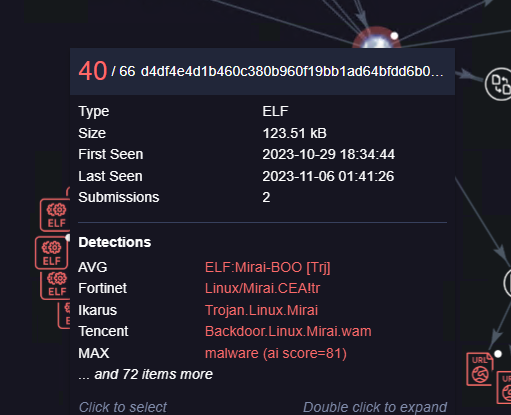
Analysis of the sample
As we analyse the domain and IP address associated with recent command and control (C&C) operations, a critical question emerges: Are we witnessing the birth of the next generation of the Mirai botnet, or is this something entirely different? To answer this, we need to conduct a deeper dive into the internals of the malware involved, particularly given that it’s written in GoLang — a language increasingly favored by modern threat actors for its cross-platform capabilities and robust concurrency features.
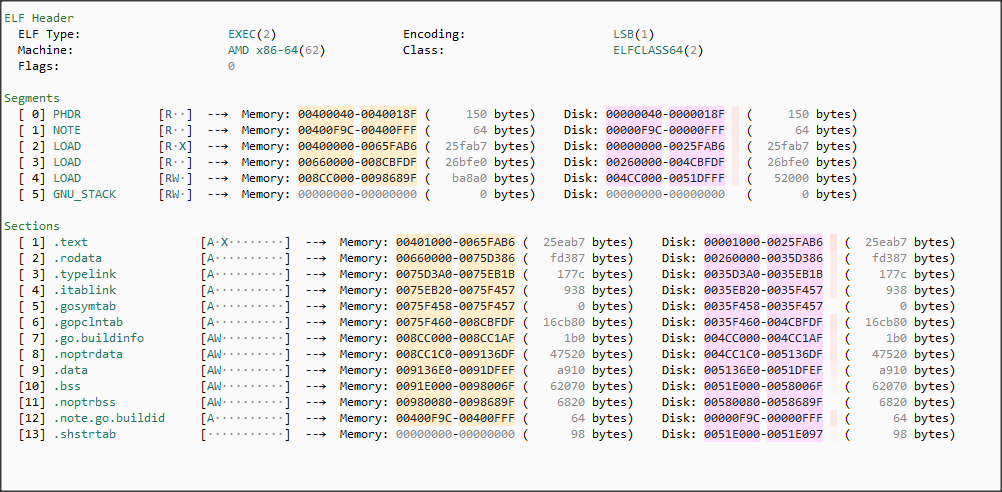
In the course of our investigation, it has become apparent that the malware in question has been widely classified by various security vendors as Kaiji. Given the strong consensus among the AV community, it’s prudent to align our analysis with these findings, while still examining the nuances that distinguish Kaiji from other threats like Mirai.
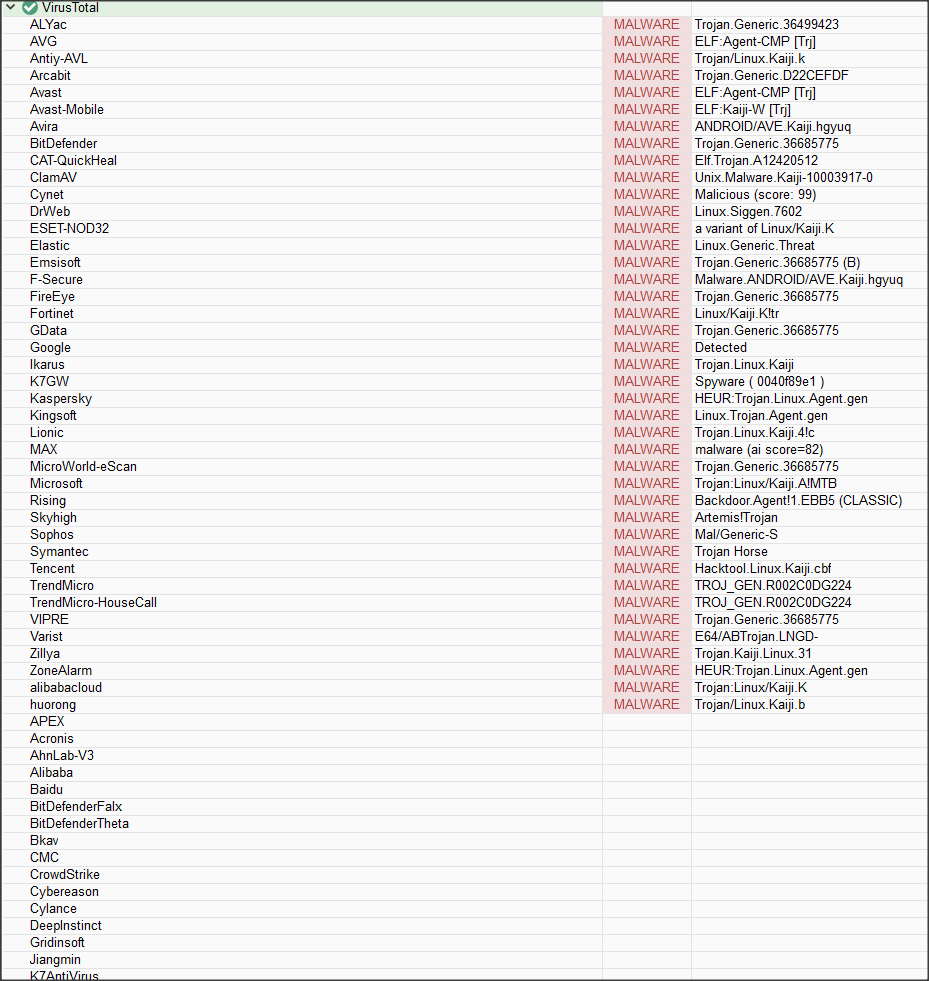
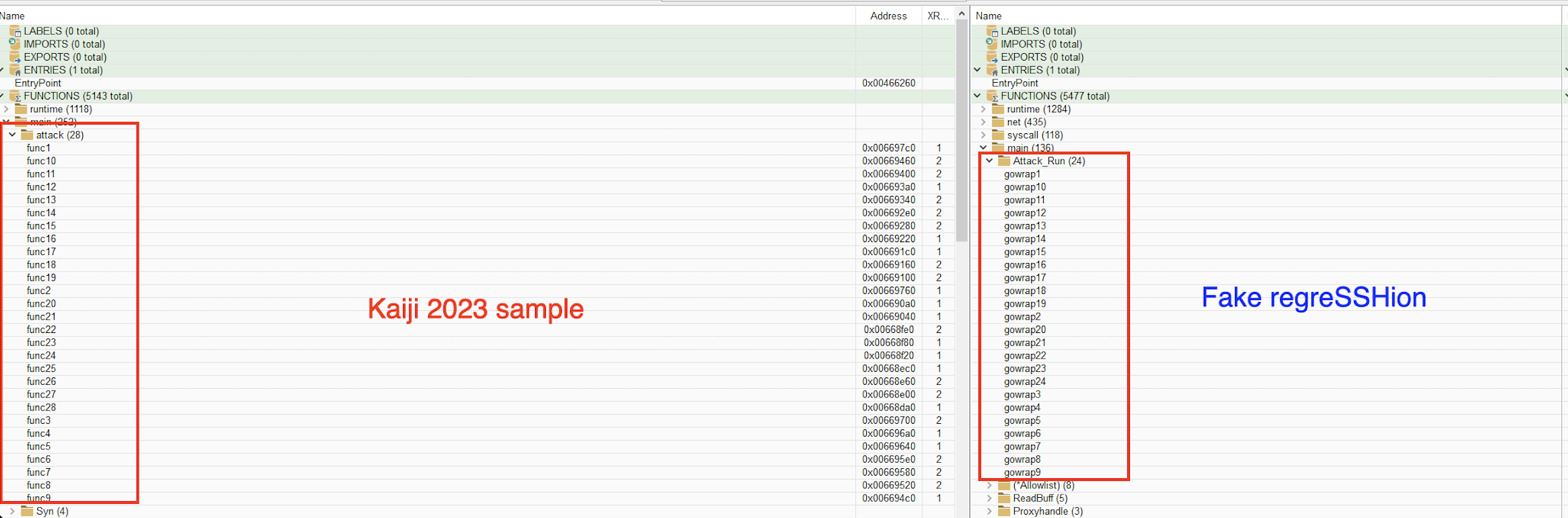
lets take a deeper look at our sample and compare it with Kaiji sample discovered in 2023.
SHA-256 - 88b679212f9fe3d97c5d2f0755f5b1f82ae7493c4295e1477522d1bd3844c314
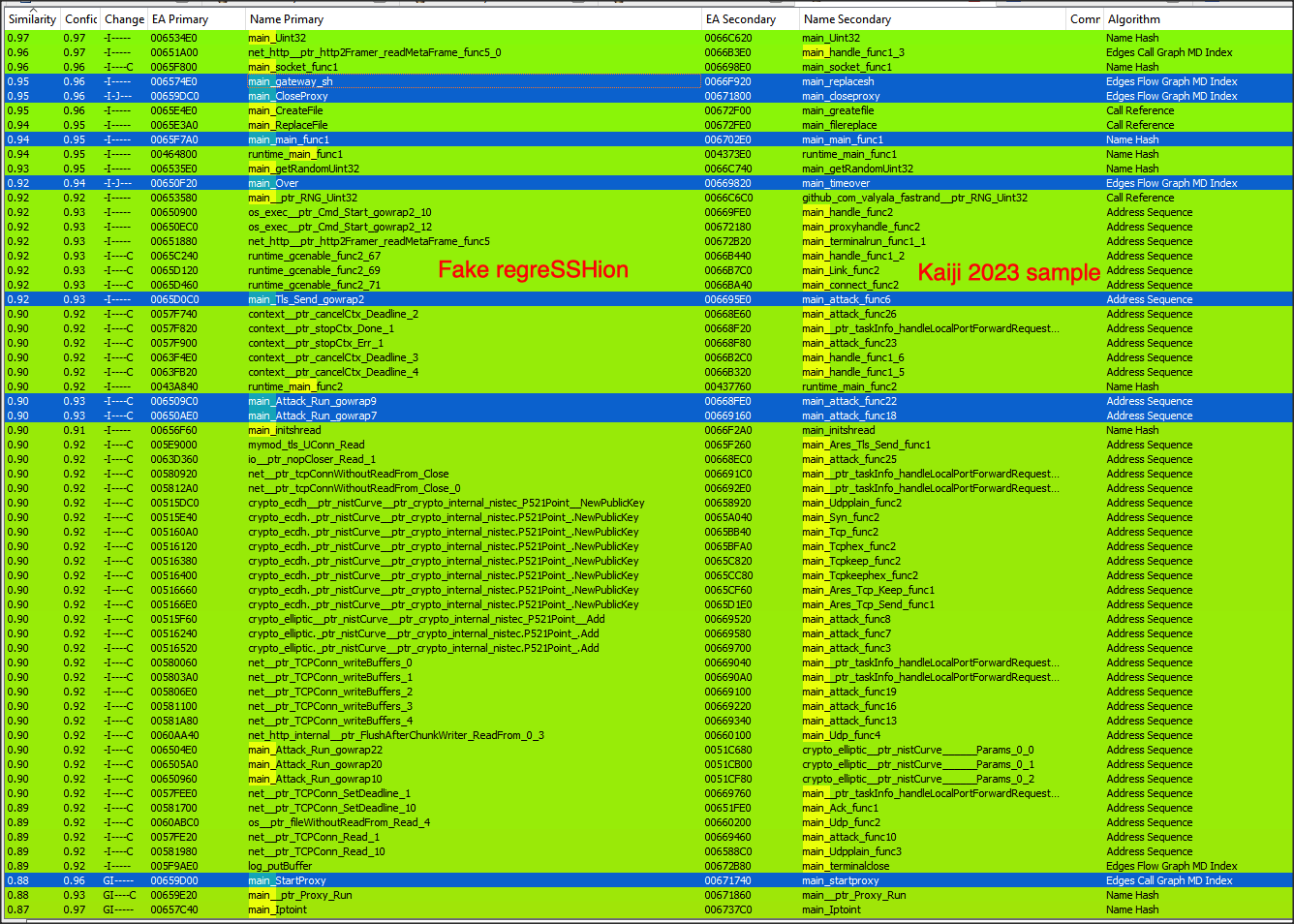
Supported commands -
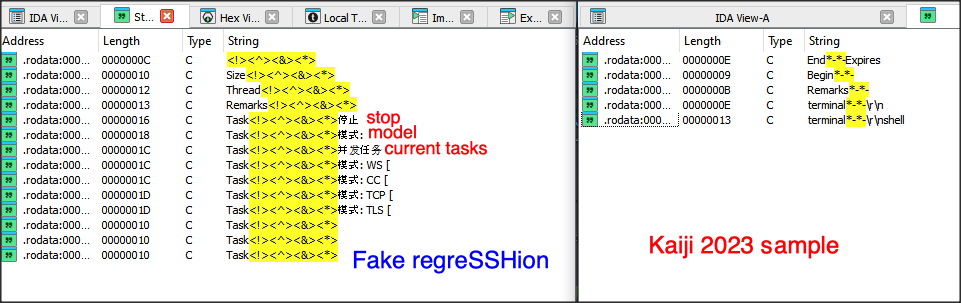
Dropped files and persistence -
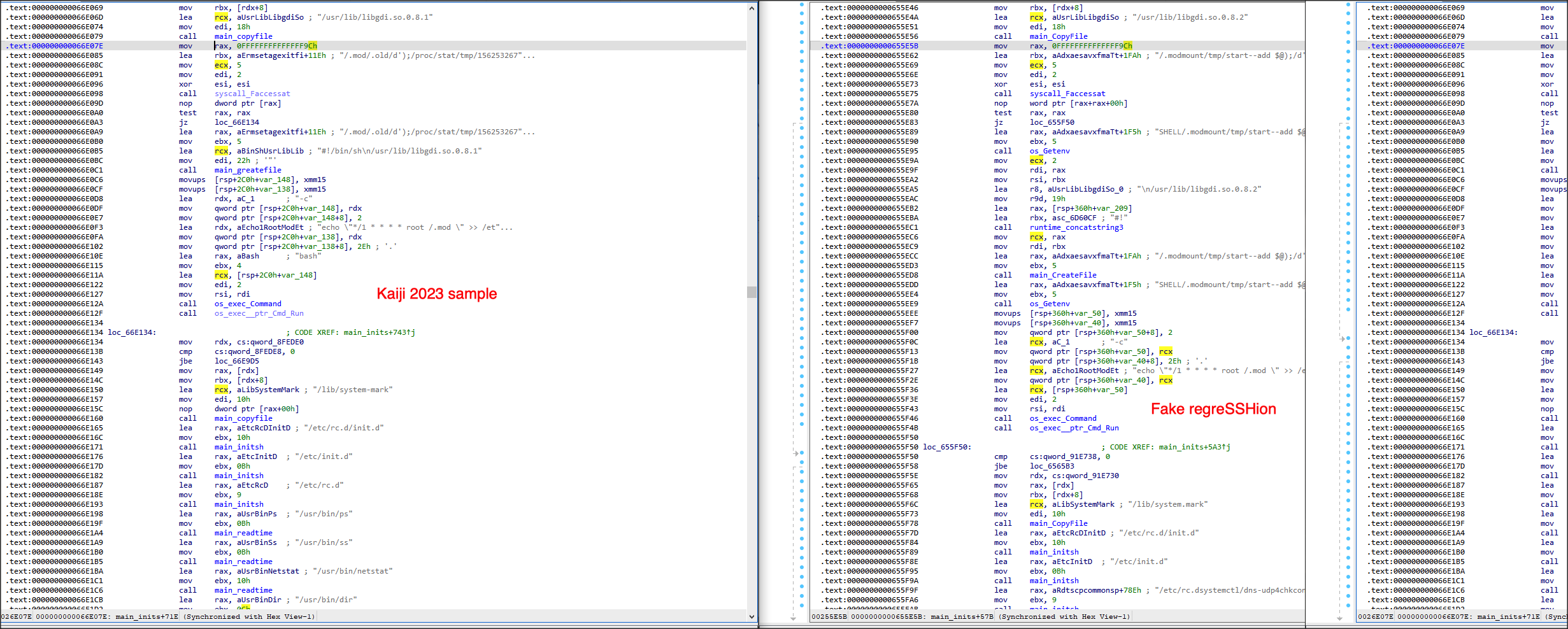
As we can see these samples are indeed very similar with a few minor differences e.g. configuration param delimiter, number of supported attacks, dropped files names and locations.
DDOS Attacks supported by the Hesoid (the new strain of Kaiji)
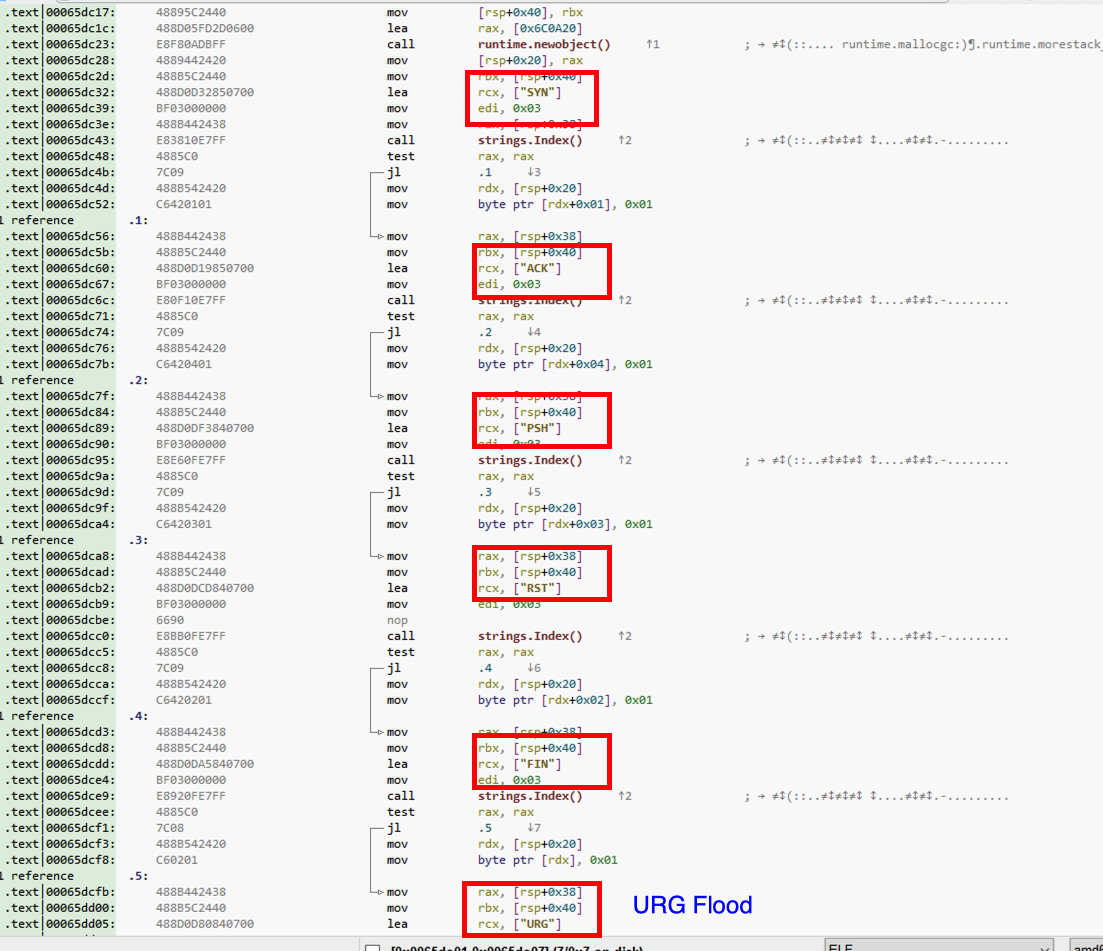
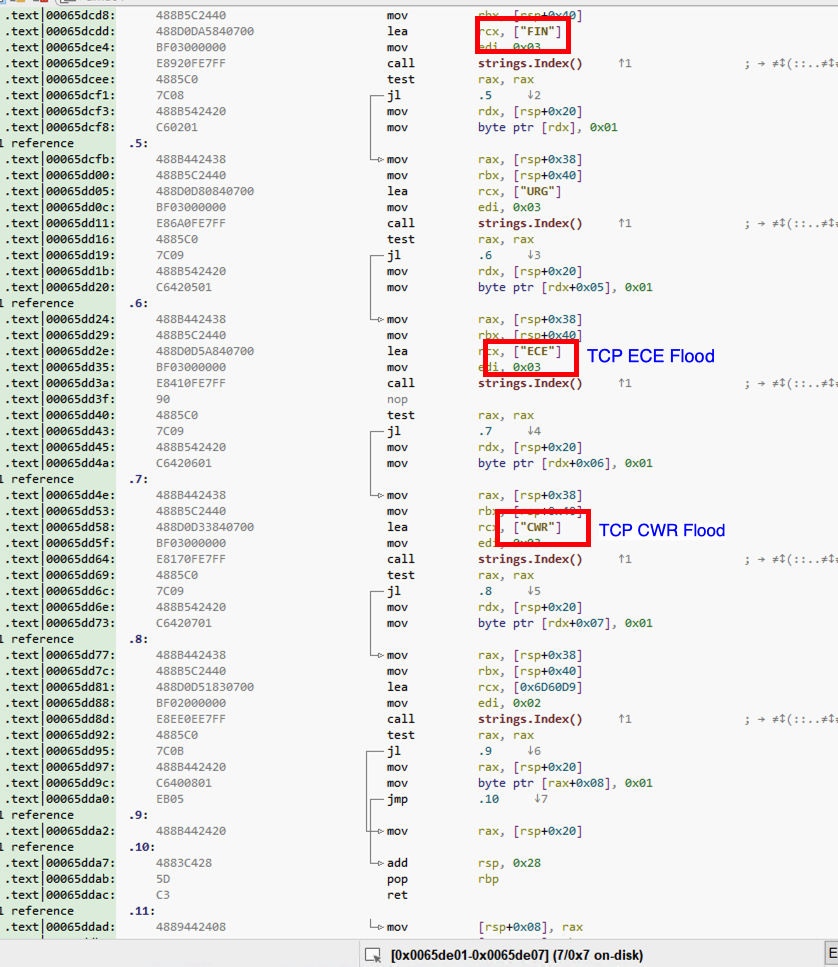
Configuration
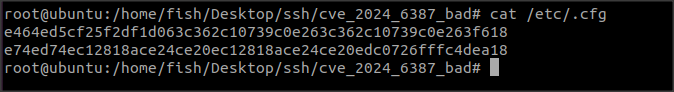
Hesiod stores its configuration in /etc/.cfg file.
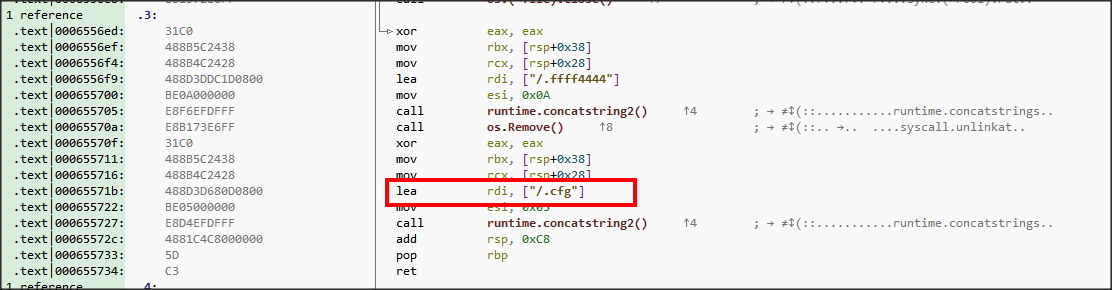
The main.getfff() function is used to revive the encrypted configuration blob from the file and decrypts it using main_XorDec()
Decrypted config -
Provenance
Kaiji, originally identified by the Intezer team in 2020 and attributed to China, stands out as a significant development in IoT-targeted malware. This attribution was based on the use of Chinese function names and comments within the code samples. Kaiji has played a foundational role in the evolution of IoT botnets, serving as the precursor to what is now known as the Chaos botnet. While Chaos is a more recent development, it retains much of Kaiji’s core functionality as a powerful DDoS botnet, while also incorporating several enhancements and adaptations. To fully grasp this progression, it’s crucial to revisit Kaiji’s impact and characteristics as a pioneering force in the IoT malware landscape.
Evolution to Chaos: Retaining and Expanding Capabilities
The Chaos botnet, considered a descendant of Kaiji, retains much of the latter’s functionality, particularly its DDoS capabilities. However, Chaos has evolved with additional features and more sophisticated techniques, making it a more versatile and dangerous threat. While Kaiji was primarily focused on DDoS attacks via compromised IoT devices, Chaos appears to have incorporated new vectors and capabilities, allowing it to exploit a broader range of targets and perform more complex operations.
The Role of Social Engineering and RCE
In analyzing the current variant of Kaiji, it’s clear that the botnet’s developers have not only retained but also refined their approach. While the focus remains on SSH as the primary attack vector, there has been a notable shift toward incorporating social engineering tactics. This shift marks a significant development in their strategy, aiming to deceive more sophisticated targets, such as security researchers.
The question of whether Kaiji’s effectiveness lies solely in its DDoS capacity or if it extends to more deceptive tactics is particularly relevant here. While targeting security researchers with a DDoS botnet might seem questionable in terms of impact, the retention of remote code execution (RCE) capabilities within Kaiji suggests a deeper motive. By engaging social engineering tactics, the attackers could be attempting to deceive researchers into unknowingly deploying malicious payloads, thus compromising their systems or networks for more strategic purposes beyond just DDoS attacks.
Conclusion: Kaiji’s Place in the Botnet Evolution
Kaiji, as an independently developed botnet, represents a significant departure from the Mirai variants that have dominated the IoT malware space since 2016. Its use of GoLang, strategic targeting of SSH, and evolution into a tool capable of both DDoS and RCE attacks marks the continued evolution of modern botnets.
As we observe the emergence of the Chaos botnet, which builds on Kaiji’s foundation, it’s clear that these threats are not static. They evolve, adapting new tactics and capabilities that make them more challenging to defend against. Whether through DDoS, RCE, or social engineering, the threat landscape continues to shift, demanding vigilance and adaptability from cybersecurity professionals.
In summary, Kaiji’s legacy lives on in Chaos, and its role as a GoLang-written DDoS botnet with sophisticated attack vectors underscores the ongoing evolution of IoT-targeted malware. As these threats continue to evolve, so too must our defenses, ensuring that we remain one step ahead in this ongoing cyber arms race.
The shift towards using languages like GoLang and Rust in malware development presents a significant challenge for security researchers. These languages, with their unique structures and modern design principles, make reverse engineering more complex and time-consuming. This difficulty underscores the growing sophistication of contemporary malware and the evolving landscape that defenders must navigate.
For those interested in diving deeper into these challenges, Nicole Fishbein, a Security Researcher at Intezer, and Juan Andrés Guerrero-Saade, AVP of Research at SentinelLabs, SentinelOne, presented cool research at this years BlackHat USA titled “Project XAC: Deoxidizing the Rust Malware Ecosystem